Protecting cloud environments is not possible without ensuring application security. This is precisely the topic for this post, which is the last part of a series of technical blogposts that our expert Mario de Felipe has been preparing to help companies move their workloads to the cloud safely.
The challenge for any company today is an increasing number of hacker attacks added to higher regulatory requirements for security and compliance controls.
Today, it’s clear for any SAP organization that Roles and Authorizations only does not protect an SAP S/4HANA environment, this must be added to a Perimeter and IT infrastructure security while at the same time analyzing the huge amount of events coming from the SAP S/4HANA Business Applications.
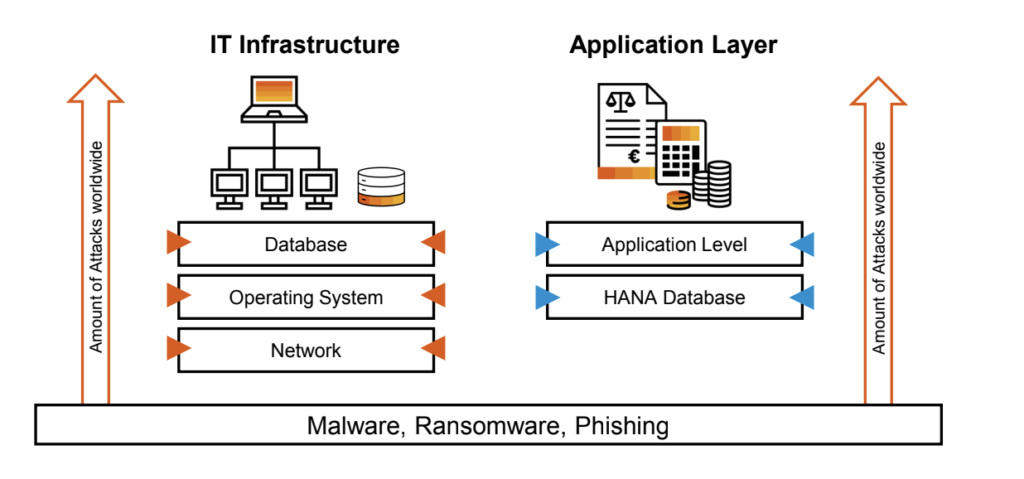
Processing all SAP log events in a non-SAP SIEM solution brings an additional challenge since costs can be high when SIEM solutions are licensed based on the log volume and the volume of logs provided out of the SAP applications is not only big but difficult to understand its semantic and integrate into these offers, for this SAP created Enterprise Threat Detection.
Enterprise Threat Detection
While traditional SIEM solutions like HP Arcsight, IBM Q-Radar or Splunk have focused on Database, OS and Network logs, ETD solely focuses on SAP application and HANA database. ETD can detect user data tables with weak password hashes downloaded on file system or brute force attack used to access SAP with superuser permissions, among many other security checks.
ETD can also help in combination with the SAP standard Security Audit Log (aka SAL) by receiving and archiving all logs created by SAP and providing a higher level of modelling.
GRC and Identity Management
GRC and IDM are not new SAP products, both have been around for many years and a lot of literature is available already, but it’s always good to remind what is the purpose of GRC and Identity Management, while GRC focuses on streamlining and automating risk management and compliance processes like FireFighter users and workflows, Identity Management focuses on ensuring and maintaining the identity of any enterprise user around the company, in the CMD (Create, Modify and Delete) process.
SAP Cloud Identity Access Governance
Not only SAP is evolving both GRC and IDM (both have a roadmap) but also new cloud products were launched like SAP Cloud Identity Access Governance (SAP IAG) which provides a good alternative for GRC Access Control.
SAP Cloud Identity Access Governance is a cloud-based tool for admins to use in simplifying governance processes. Functionality includes continuous access analysis, user assignment optimization, preconfigured audit reporting, among others.
SAP Code Vulnerability Analyzer
Also known as SAP NetWeaver AS Code Vulnerability Analysis (CVA), the SAP Code Vulnerability Analyzer is an ABAP add-on that analyzes source code and secures it from potential attacks before delivering applications to end users.
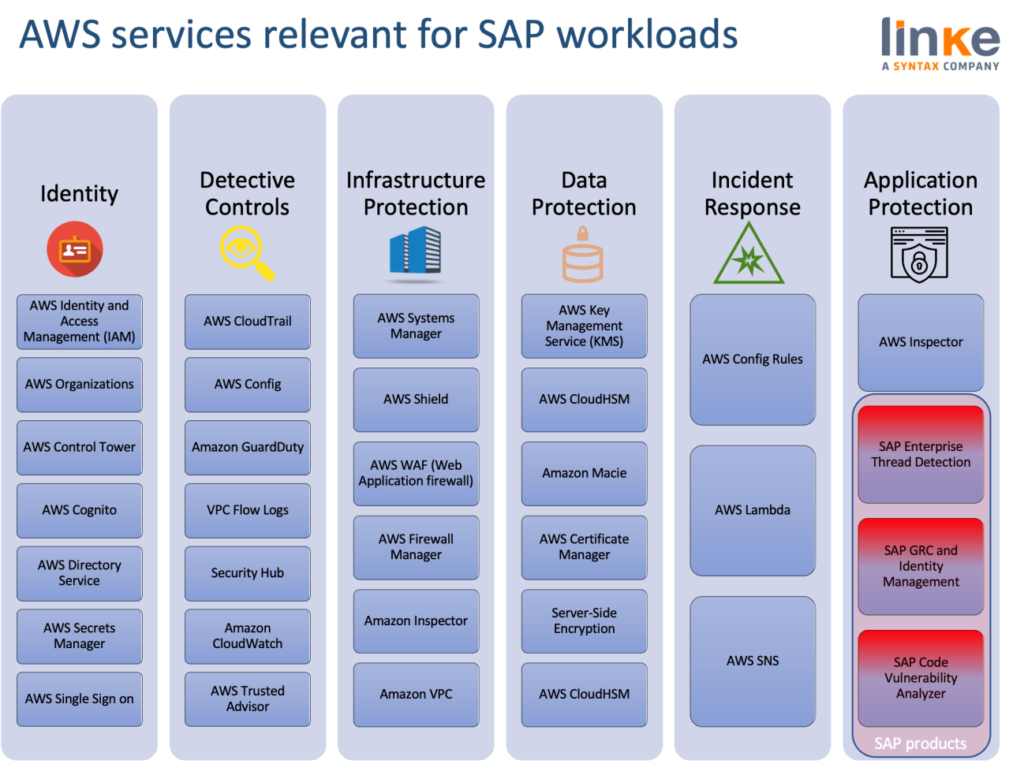
How AWS can help to solve SAP top Security concerns
We organized this year a webinar describing how a combination of SAP Enterprise Threat Detection with Amazon Guard Duty can be leveraged by Amazon Macie.
Amazon Macie is a service that uses machine learning and pattern matching to discover and protect sensitive data. As organizations manage growing volumes of data, identifying and protecting their sensitive data at scale can become increasingly complex, expensive, and time-consuming. Amazon Macie automates the discovery of sensitive data at scale and lowers the cost of protecting data.
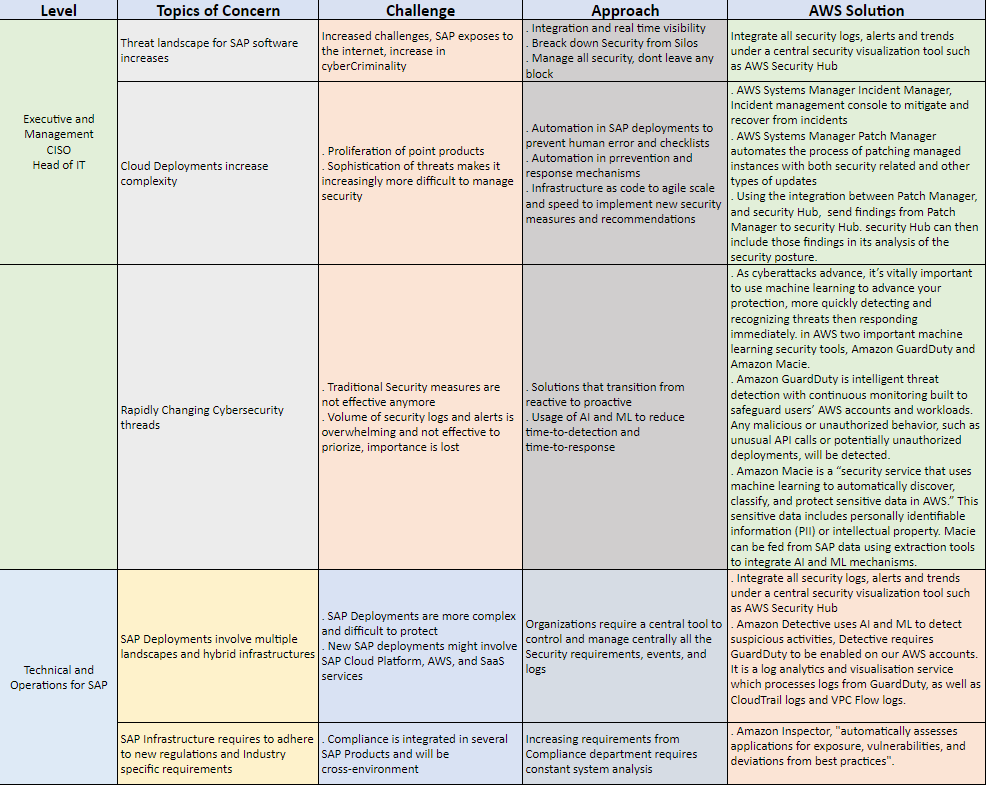 8 Golden rules for a safe SAP on AWS landscape:
8 Golden rules for a safe SAP on AWS landscape:
- Perform Log Analysis with Amazon GuardDuty.
- Identify Root Cause and suspicious with Amazon Detective.
- Classify and Protect Sensitive Data with Amazon Macie.
- Stay Tested and Protected with Amazon Inspector.
- Get a Single Unified View with AWS SecurityHub.
- Follow Best Practices with AWS TrustedAdvisor.
- Know Your Configurations with AWS Config.
- Patch frequently with AWS Systems Manager.
Vincent Doux from SAP, Steve Quinn from AWS EMEA and Benoit Ohron from Syntax, discussed during that webinar how to secure SAP systems data on the AWS platform, the session can be accessed here.
Following the below links you can also access to the rest of those post series based on SAP on AWS security:



