Protecting data and workloads is a top priority for all companies that migrate their systems to the cloud, and this topic is addressed by our expert Mario de Felipe in the fourth post of the series of 5 posts that we are dedicating to security in AWS.
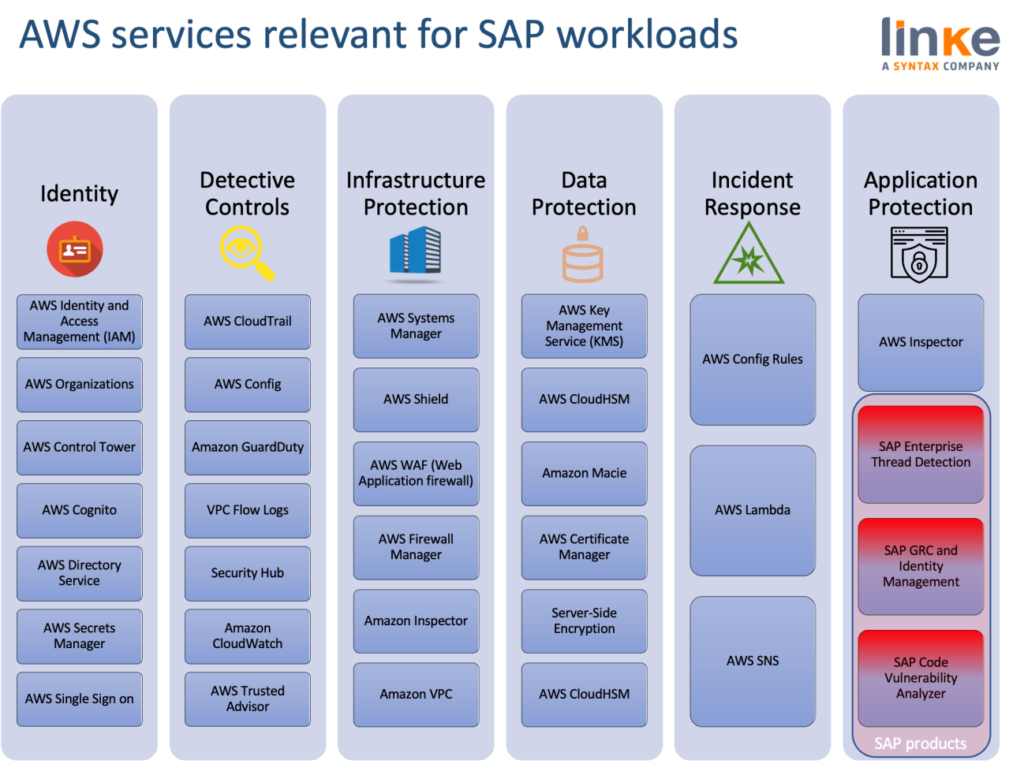
Following the three previous blogpost, focused on Identity and Access Management, Detective Controls and Incident Response and Infrastructure Protection, this week’s review is about Data Protection.
In AWS, there are a number of different approaches to consider when addressing data protection. They are:
- Data Classification.
- Encryption/tokenization.
- Protecting data at rest.
- Protecting data in transit.
- Data backup/replication/recovery.
Data Classification
Data classification provides a way to categorize organizational data based on levels of sensitivity. This includes understanding what data types are available, where the data is located, and access levels and protection of the data (for example, through encryption access control).
Understanding and using resource tags is often ignored by AWS users but they are a simple and powerful method of organizing our AWS assets.
Tagging is applied to cloud resources providing a bespoke metadata schema to logically organise and group resources. This is critical for automation, security, and financial reporting purposes.
All cloud resources, that can be tagged, must be configured with tags. There should be no exception to this standard and tags should be applied at build time. An example of Tagging requisites.
| Tag Name | Description | Example | Value |
| Application ID | Unique business identified for the application | APP00001 | What is the Application ID for your application? APP0001008 |
| Application Name | Name of the application, service, or workload the resource is associated with. The same name present in the CMDB | SAPERP | What is the Application Name for your application? SAP ERP |
| Business Unit | Top-level division of Company that owns the application resource. | Beverages | What is the Business Unit? |
| Department | Department that owns the application resource. | Beverages Digital | What is the Department? Global Applications |
| Cost Center | Cost Center ID – used by Finops for cross charging | US001 | What is the Cost Center for your application? USXXXXXX |
| Environment | Deployment environment of this application, workload, or service. | environment=Prod | Applicable environment(s) (select by deleting non-applicable):
☐ Prod ☐ Con ☐ Dev ☒ Test ☐ Que ☐ Sandbox |
Besides resource tags, the primary data classification tool offered by AWS is Macie:
Amazon Macie
Amazon Macie is a security service that uses machine learning to automatically discover, classify, and protect sensitive data in AWS. Macie recognizes sensitive data such as personally identifiable information (PII) or intellectual property and provides you with dashboards and alerts that give visibility into how this data is being accessed or moved.
Encryption/Tokenization
Data protection refers to protecting data while in-transit (as it travels to and from Amazon S3) and at rest (while it is stored on disk in Amazon S3). AWS Key Management Service (KMS) gives a centralized control over the encryption keys used to protect your data.
We can create, import, rotate, disable, delete, define usage policies for, and audit the use of encryption keys used to encrypt your data. AWS Key Management Service is integrated with most other AWS services making it easy to encrypt the data you store in these services with encryption keys you control.
Encrypting Amazon resources such as, EBS volumes for data and databases, S3 for objects or backups is a must and also required to comply with regulations including the General Data Protection Regulation, or GDPR, with key management capabilities that include regional isolation.
Also, SAP provides Data Custodian Key Management Service, a Cloud-Ready Encryption and Key Management as a Service offering. SAP Data Custodian is described and presented by our experts on this article.
We don’t want to close this chapter without bringing one topic into account, it’s a good practice disabling IMDSv1 on our EC2 instances to prevent a Capital One-like data breach. IMDSv2, the Amazon Instance Metadata Service is used by agents, such AWS Data Provider for SAP, to collect performance-related data from AWS services. It makes this data available to SAP applications to help monitor and improve the performance of business transactions.
Provide SSL inspection
Most HTTP traffic is SSL encrypted, and SAP has embraced HTTP as a modern protocol for users to access S/4 applications. Today more than 60% of malware is encrypted though. In SAP, Web Dispatchers are used by SAP to load balance SAP’s Fiori systems. The Web Dispatchers create a larger attack surface and vulnerabilities for common Open Web Application Security Project (OWASP) attacks.
An Application Load Balancer is normally placed as an external zone acting as the entry point for Web Dispatcher’s HTTP/HTTPS requests. AWS Shield can protect the Web Dispatcher and SAP NetWeaver Gateway from common web exploits, especially if it’s used in conjunction with AWS WAF in the load balancer. AWS Shield is a managed distributed denial of service (DDoS) protection service that safeguards web applications running on AWS.
Securing Data at Rest
Data at rest includes inactive data that is stored physically in any digital form (e.g. databases, data warehouses, spreadsheets, archives, tapes, off-site backups, mobile devices, etc.). Multiple AWS services provide built-in integration with AWS KMS to allow easy encryption of your persistent storage.
Again with SAP Data Custodian, using Data Custodian, customers can leverage Customer-controlled encryption keys for SAP HANA and SAP applications at rest SAP Data Custodian key management service has native integration with the SAP HANA database , starting with HANA 2.0 SP05, aiming to lock our database for any unauthorized access.
Securing Data in Transit
Data in transit is any data that gets transmitted from one system to another. This includes communication between servers within your environment as well as communication between other services and your end users. By providing the appropriate level of protection for your data in transit, you protect the confidentiality of your application’s content. When protecting your data in transit, selecting protocols that implement the latest version of Transport Layer Security (TLS) is a common best practice.
AWS services provide many HTTPS endpoints for communication, thus providing encryption in transit when communicating with the AWS APIs. AWS Certificate Manager (ACM) service provides you the ability to manage and deploy certificates for your domains.
AWS Certificate Manager (ACM) is a service that lets you easily provision, manage, and deploy public and private Secure Sockets Layer/Transport Layer Security (SSL/TLS) certificates for use with AWS services and your internal connected resources. SSL/TLS certificates are used to secure network communications for key SAP products like Web Dispatcher, SAP ICM or SAP Gateway, it’s one of the required steps to setup a Fiori environment
You can checkout this blogpost from AWS architects Ferry Mulyadi and Yoshihisa Nakatani to setup such an architecture.
Data Backup/Replication/Recovery
“If you store 10,000 objects with us, on average we may lose one of them every 10 million years or so” that’s Amazon describing S3 capabilities. Amazon S3 and Glacier are a secure, durable, and extremely low-cost cloud storage service for data archiving and long-term backup.
SAP-certified backup and restore solutions include HANA DB running in the cloud or on-prem directly to S3. CxLink Backup, listed on AWS Marketplace and SAP Store include HANA, Oracle and Sybase full, incremental, and differential backup.
At additional cost compared to S3, EBS Snapshots also provide backup and recovery possibilities, Snapshots let you back up your volumes attached to EC2 instances.
As SAP experts on AWS, we are committed to helping organisations achieve high levels of security, bringing the benefits of the cloud to those SAP workloads. If you want to know more about innovative and cloud-native solutions in terms of security, you can watch this webinar on demand.



